Intrusion Detection System Pdf
Intrusion detection system pdf. As network attacks have increased in number and severity over the past few years intrusion detection systems have become a necessary. Del Castillo Trisha Mari L. System Administration and Module Development Jamie Cameron Implementing CIFS.
In addition organizations use IDPSs for other purposes such. With Snort Advanced IDS Techniques Using Snort Apache MySQL PHP and ACID perens_seriesfm Page 1 Thursday April 10 2003 143 AM. Iv Acknowledgments We thank Lori Gill Office Coordinator in G021 for her thorough copy editing of our final draft.
Intrusion Detection Systems IDS Seminar and PPT with pdf report. More specifically IDS tools aim to detect computer attacks andor computer misuse and to alert the proper individuals upon detection. PDF On Jul 26 2019 Michael Coole and others published Intrusion detection systems Find read and cite all the research you need on ResearchGate.
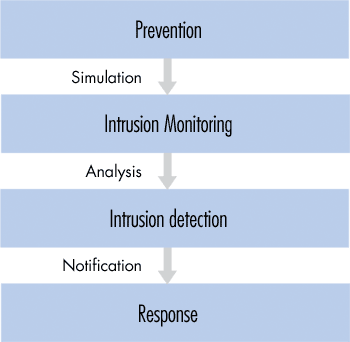
An intrusion detection system IDS is a system used to detect unauthorized intrusions into computer systems and networks. Intrusion Detection System IDS is a software that monitors networks or activities of a system and look up unusual behaviors and alarm in case of detecting malicious activities 2. 1526 OWERRI IMO STATE OCTOBER 2014 INTRUSION DETECTION AND PREVENTION SYSTEMS IN AN ENTERPRISE NETWORK BY OKEHIE.
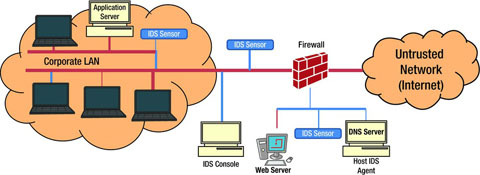
INTRUSION DETECTION AND PREVENTION SYSTEMS IN AN ENTERPRISE NETWORK BY OKEHIE COLLINS OBINNA 20091649415 DEPARTMENT OF COMPUTER SCIENCE SCHOOL OF SCIENCE FEDERAL UNIVERSITY OF TECHNOLOGY P. Intrusion detection systems IDSs are software or hardware systems that automate the process of monitoring the events occurring in a computer system or network analyzing them for signs of security problems. In addition organizations use IDPSs for other purposes such as identifying problems with security policies.
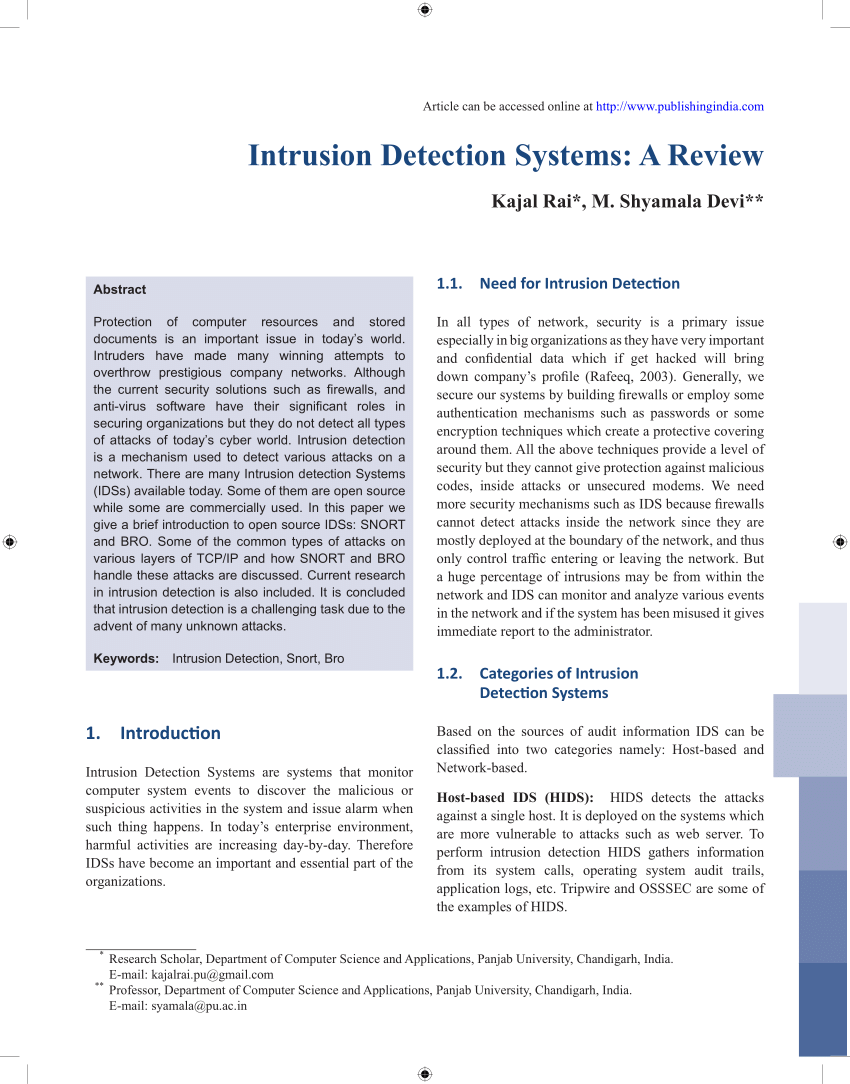
Intrusion detection and prevention systems IDPS are focused on identifying possible incidents logging information about them attempting to stop them and reporting them to security administrators. It is a software application that scans a network or a system for harmful activity or policy breaching. To develop Intrusion Detection System using K-Means clustering algorithm.
The intrusion detection system will normally be designed to provide the earliest possible warning of an intrusion attempt. From Stateful Firewall to Network Intrusion Detection System Fanglu Guo Tzi-cker Chiueh Computer Science Department Stony Brook University NY 11794 fanglu chiueh cssunysbedu Abstract Computer network is already an indispensable part of our modern life.
The different sources of event information used to determine whether.
As network attacks have increased in number and severity over the past few years intrusion detection systems have become a necessary. More specifically IDS tools aim to detect computer attacks andor computer misuse and to alert the proper individuals upon detection. IDS do exactly as the name suggests. Describing system hardening constitute intrusion detection systems. In addition organizations use IDPSs for other purposes such as identifying problems with security policies. To keep our network run smoothly we need to know its condition. V Table of Contents Section Page Introduction 1 Background 1 Disclaimer 2 Scope 2 Processing Requirements 3. With Snort Advanced IDS Techniques Using Snort Apache MySQL PHP and ACID perens_seriesfm Page 1 Thursday April 10 2003 143 AM. Any malicious venture or violation is normally reported either to an administrator or collected centrally using a security information and.
Any malicious venture or violation is normally reported either to an administrator or collected centrally using a security information and. Intrusion detection is the act of detecting unwanted traffic on a network or a device. Intrusion detection and prevention systems IDPS 1. Intrusion Detection System IDS is a software that monitors networks or activities of a system and look up unusual behaviors and alarm in case of detecting malicious activities 2. With Snort Advanced IDS Techniques Using Snort Apache MySQL PHP and ACID perens_seriesfm Page 1 Thursday April 10 2003 143 AM. The intrusion detection system basically detects attack signs and then alerts. Intrusion detection system network monitoring and assessment NMA CSAP21.





































Post a Comment for "Intrusion Detection System Pdf"